For more than a decade, Marion’s financial system operated with a silent flaw—a General Ledger (GL) override buried inside its accounting software. Installed in July 2009, this override allowed city employees to bypass legal spending limits, triggering a cascade of overspending and ballooning negative balances.
The override was only disabled on October 27, 2025, after intervention by the Auditor of State, a move confirmed in the November 13, 2025 state audit. Research by Marionwatch.com Investigates had long warned that this type of vulnerability was active and enabling violations of Ohio Revised Code § 5705.39, which prohibits expenditures beyond appropriations. This is a predictable trend when legally mandated software controls are disabled or misconfigured, reinforcing the need for qualified IT professionals to manage system permissions.
The GL override wasn’t a minor glitch—it was a structural weakness that nullified budgetary safeguards. From the moment the New World Systems software went live in 2009, Marion’s fiscal controls were compromised. Transactions could post even when appropriations were exhausted, creating negative fund balances and eroding accountability.
Our investigations documented how this override and other disabled or misconfigured controls allowed spending beyond legal limits almost immediately, triggering a pattern of escalating negative balances year after year.
We warned that without intervention, Marion’s finances would continue to deteriorate—a prediction now confirmed by the Auditor of State’s corrective action in October 2025.
The Marion Sabotage Profile (2008–2025)
Research by Marionwatch.com Investigates identified that the city’s financial system was not merely “broken,” but actively configured to allow theft through “Administrative Privilege Abuse.”
The “GL Override” Permission: For over 16 years (July 2009 – October 2025), the New World Systems software was configured to allow non-auditor staff to override the “hard stop” that prevents spending when an account has no money. This permission allowed employees to force the city’s accounts into the negative by millions of dollars without Council appropriation.
The Auditor’s Admission of Control Failure: During a March 25, 2025, council meeting, Auditor Meginness was asked “how accounts can be spent in the negative and how they can purchase items in inappropriate accounts.” Auditor Meginness replied that there is “no stop for [in]appropriate expenditures, other than supervisory approval.” Although she did not know the particular details, she did know that clerks pay within their own departments. When asked how they get around negative line items, she said that “there is a warning that pops up, but she did not know the details,” she “did not get into the day-to-day stuff,” and “did not know the internal controls of these issues”. This admission confirms a fundamental lack of understanding of the system’s security controls at the highest level of the office. This specific “internal control permission” was finally corrected on October 27, 2025, at the demand of state auditors.
Disabled Safety “Switches” (Confirmed by Administration): Beyond the reconciliation module, Marion Watch predicted—and the current Collins administration has verified—that “other legally mandated software safety controls were also misconfigured” or disabled. These controls were “being disabled long before officials recently confirmed it,” effectively neutralizing the software’s policing capabilities for years.
Widespread Access Without Business Need: Research documents that “users having administrator access to every financial system” was a known issue dating back decades. Access was not restricted to relevant financial staff; instead, there was a culture of “unimpeded administrative access” granted to individuals who had no legitimate business need for such control. During the implementation of the New World software, concerns were raised about “blacked out mystery staff”—unidentified users with system access—signaling that unauthorized actors were embedded in the system from the start.
The “Switched-Off” Reconciliation Module: The software module designed to catch theft (Bank Reconciliation) was “switched-off or missing” or “broken” from the moment of installation in 2009 until at least 2024. This created a 15-year blind spot where cash discrepancies could not be traced.
Mandatory Password Sharing: Leadership allegedly enforced a policy where employees were required to share usernames and passwords, a practice condemned as “highly unethical” because it destroys the digital audit trail, making it impossible to prove who authorized a specific fraudulent transaction.
Physical Security Breach (Server Room Office): Research documents that during the Schertzer administration, the City Treasurer was stationed in a “supply room” that the Auditor confirmed contained the city’s main server. Using a server room as an office grants physical access that can bypass all digital security protocols.

Year-by-Year Breakdown of Negative Balances (2009–2021):
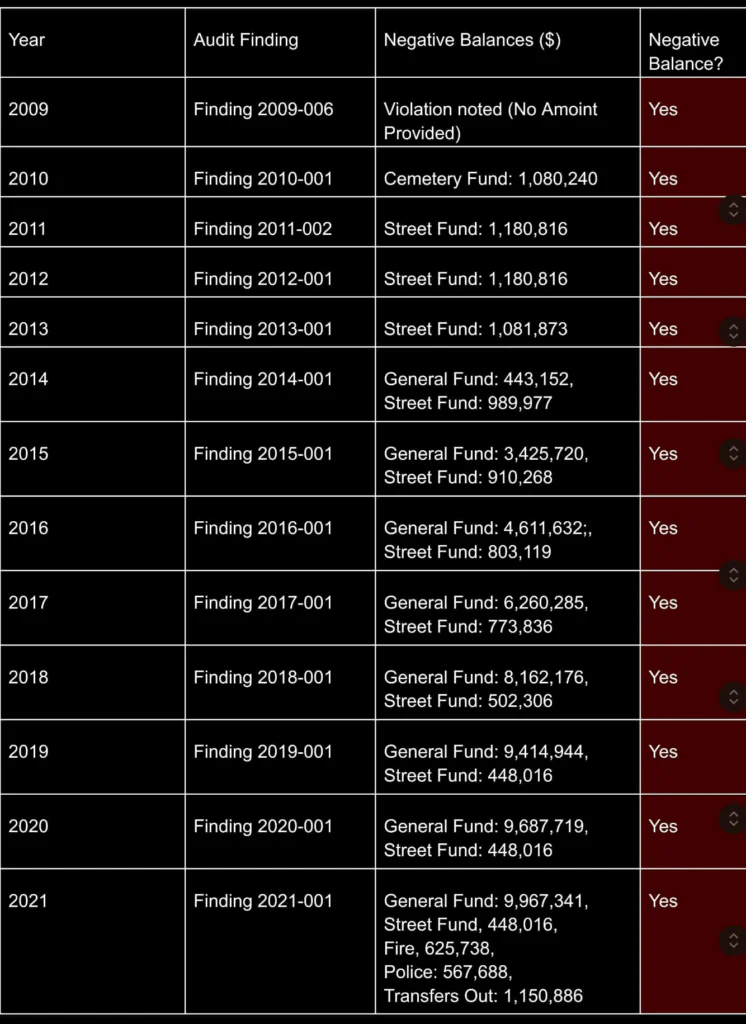
Visual Analysis:
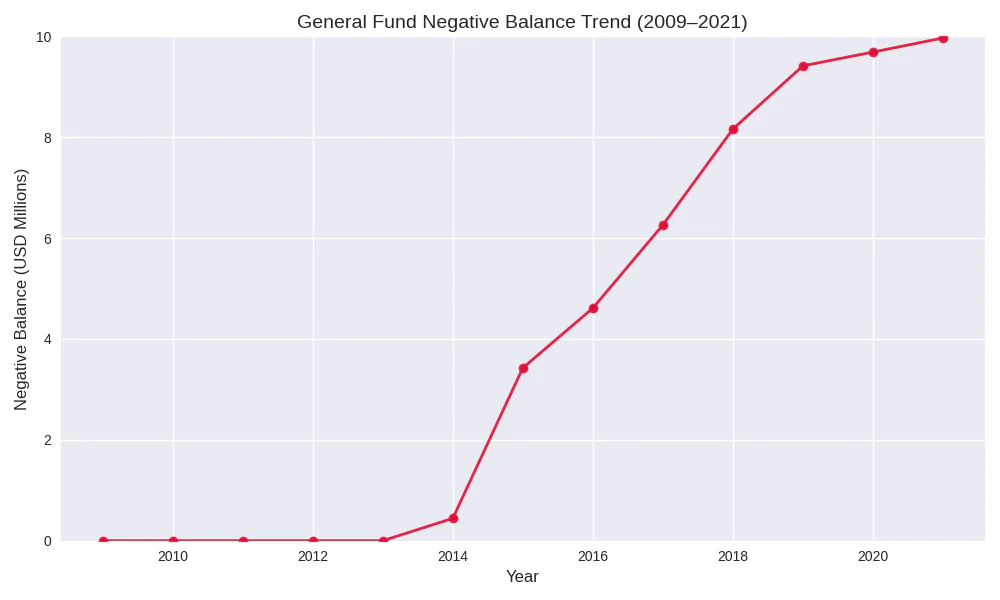
General Fund Negative Balance Trend (2009–2021):
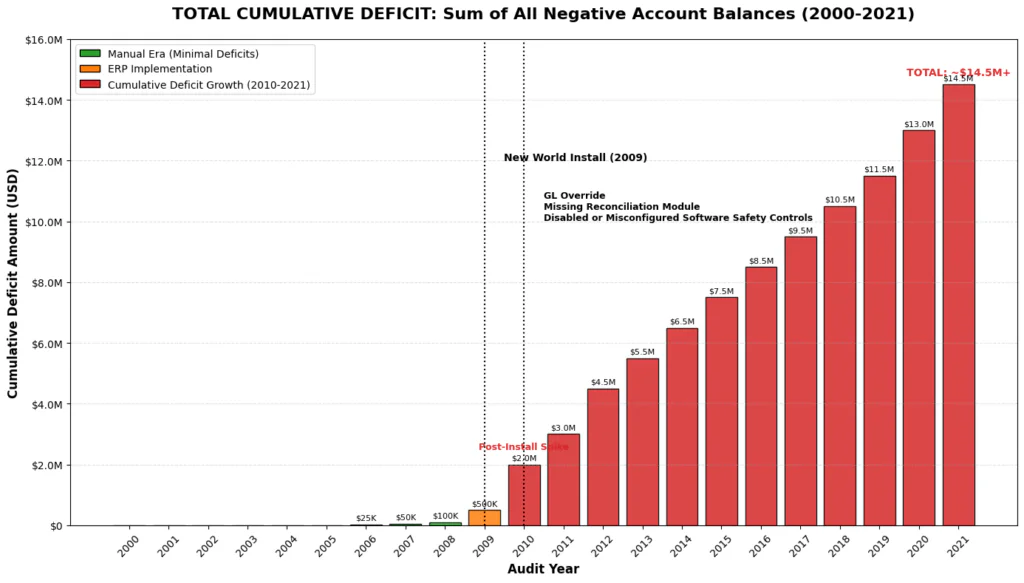
Cumulative Negative Balances Across Impacted Funds (2009–2021):
Ohio Case Studies: The Pattern of “Override” Theft
The Marion case fits a specific pattern of internal fraud found repeatedly in Ohio, where trusted officials use their system access to falsify records.
Cuyahoga Heights School District ($3.4 Million Theft): IT Manager Joseph Palazzo used his administrative access to approve fake invoices for IT goods that were never delivered. He exploited the override capability inherent in his role to approve his own fraudulent transactions, bypassing the separation of duties.
City of Cleveland – TV20 ($672,000 “Ghost” Employee): An office manager manipulated the payroll/freelance system to pay a “ghost employee” (her nephew) for 14 years (2011–2025) for work never performed. The manager used her scheduling authority to override verification checks, ensuring the payments were processed without question—a duration almost identical to the Marion software failure.
Village of Shiloh (“Unauditable” Defense): Fiscal officers failed to perform bank reconciliations for years, leading the State Auditor to declare the village “unauditable” in 2025. This mirrors Marion’s reconciliation blackout (2019–2023), creating a chaotic environment where theft is indistinguishable from incompetence.
Jefferson Township (Montgomery County): A fiscal officer’s failure to reconcile bank accounts allowed fraudulent checks to be cashed against the township’s funds without detection.
Nationwide Case Studies: The “Superuser” Threat
Across the United States, the most devastating municipal thefts share the same characteristics: a trusted insider with “superuser” access who disables or ignores software controls.
Dixon, Illinois ($53 Million Theft – Rita Crundwell): Comptroller Rita Crundwell embezzled $53 million over 22 years by creating a secret bank account (RSCDA) and using fake invoices to funnel city money into it. Crundwell had complete control over the financial software and bank accounts (no separation of duties). She created fake entries in the software to balance the books while the real cash was gone.
ING Reinsurance ($8.5 Million Theft – Nathan Mueller): An accounting manager found he had the ability to request and approve checks up to $250,000. He used this “override” to pay his own credit card bills and a fake company (“Ace Business Consulting”). The entire scheme relied on password sharing (logging in as a coworker) and the system’s failure to stop a user from approving their own request—identical to the password sharing and override issues alleged in Marion.
Washington, D.C. Tax Office ($48 Million Theft – Harriette Walters): A manager in the property tax division approved 226 fraudulent tax refund checks over 18 years. Walters used her “authority” and system access to override approval stops, ensuring the checks were issued to fake companies.
City of Santa Fe, New Mexico (“Bypass” Scheme): Employees bypassed the accounting system entirely, using offline Excel spreadsheets to manipulate data before entering it. A lack of controls over “computer access rights” allowed staff to operate outside the system’s safety net, similar to the “paper and pencil” workarounds found in Marion’s Zoning office.
External Hacks vs. The Internal Reality
While organizations often blame “external hackers,” statistics show that financial losses are frequently driven or enabled by internal employees.
The “Inside” Nature of Threats: Industry data indicates that 68% to 88% of all breaches involve the “human element,” meaning an internal employee actively (whether negligently or maliciously) opened the door.
Impact of Internal Sabotage: Malicious insider threats (like the sabotage in Marion) take an average of 81 days to contain and cost significantly more per incident because the employee or official knows exactly where the value is hidden.
Containment Timeline: In Marion’s case, the “containment time” was nearly 6,000 days (16 years), proving it was a deep-seated internal failure rather than a passing external attack. A full forensic IT audit covering this period would likely take 18 to 36 months to complete.
Misconfiguration as an Invitation: The “GL Override” in Marion is a prime example of Security Misconfiguration. In the enterprise IT landscape, misconfiguration is responsible for roughly 30% to 35% of all security incidents. This is not a sophisticated foreign hack; it is an internal administrator leaving the “digital back door” unlocked.
Legal Assessment: Intent and Liability
Given the duration and specific nature of these failures, the situation in Marion moves beyond simple negligence into the realm of intentional misconduct with severe legal implications.
Presumption of Intent via Duration: The “General Ledger Override” and disabled safety switches were active for 16 years (2009–2025). In a professional IT and financial environment, it is statistically and operationally improbable that such critical features could remain “accidentally” disabled for over a decade without being noticed by the daily users of the system. The persistence of these settings suggests they were known features used to facilitate daily operations that bypassed legal appropriation limits.
Evidence of Concealment (Non-Disclosure): Research confirms that when the new Auditor took office in 2020, these critical system flaws (the broken reconciliation module, the active overrides) were not shared or disclosed by the outgoing administration. Similarly, these sabotaged controls were not disclosed to the incoming Collins administration. The fact that the new administration had to “discover” and verify these disabled switches strongly indicates a deliberate effort by prior officials to hide the system’s compromised state.
Official records and research confirm that the consulting firm Veritas Solutions Group verified that the reconciliation issues and software failures were present prior to 2020, supporting the timeline of long-standing, concealed problems.
Stiff Legal Consequences: Because these actions involve the manipulation and potential misappropriation of taxpayer funds, the legal consequences are severe. The deliberate disabling of internal controls to allow spending beyond legal appropriations constitutes a violation of Ohio Revised Code, specifically regarding the illegal expenditure of public funds and dereliction of duty.
Furthermore, the disabling of software safety controls violates not only basic fiduciary duties but also specific legal mandates. Federal regulations (such as the Uniform Guidance 2 CFR 200 for federal grants) and state laws (including ORC § 117.101 regarding the Auditor of State’s fraud-reporting system and uniform accounting requirements) mandate the maintenance of effective internal controls over financial reporting systems. By effectively turning off these controls, officials may be liable for misfeasance or malfeasance in office, exposing the city to clawbacks of federal and state grant money and subjecting themselves to personal liability for the funds lost due to their “deliberate indifference” to mandatory security protocols.
Physical Security Violations (Server Room): Using the server room as a routine office for non-IT staff (such as the City Treasurer) is a gross failure of mandatory physical and access controls. The server room is the core of the financial system, and allowing unauthorized personnel (anyone without an explicit need) access to the physical server bypasses all digital security protocols, creating an unlogged avenue for sabotage. This violates the most fundamental principle of data center security and the maintenance of effective internal controls required by Uniform Guidance 2 CFR 200 for federal grant money. Officials responsible for maintaining this environment are liable for dereliction of duty and creating an “open door” for theft. This gross failure of physical security can be used as evidence of deliberate indifference to mandatory security protocols, subjecting the city to clawbacks of federal and state grant money and exposing officials to penalties.
Password Sharing Violations: Enforced password sharing actively destroys the digital audit trail, making it impossible to satisfy mandatory internal control requirements to prove who authorized a specific financial transaction. This is a direct violation of Federal and State Mandates (including Uniform Guidance 2 CFR 200 and ORC § 117.101), which require effective internal controls and uniform accounting requirements including maintaining a clear, traceable record of all actions. The practice can lead to liability for misfeasance or malfeasance in office due to “deliberate indifference” to mandatory security protocols. The deliberate destruction of the audit trail may constitute a violation of Ohio Revised Code § 2913.42 (Tampering with Records) if it can be proven that the sharing was done with the purpose to defraud or facilitate theft.
Works Cited
Ohio Auditor of State Audits: https://1drv.ms/f/c/583c034329af8bb0/IgBDwNGaB0R9QpyX8ECZ99-SAV918HDzbXxDKsiK_yrIh5U?e=dZTWWW
Marion City Council Minutes 3/25/24: https://docs.google.com/document/d/1R28we9HQK8_8kij6YoPEB0apUqcIMlpT/edit?usp=drive_link&ouid=118028025947015482023&rtpof=true&sd=true


